If you want to improve your Internet privacy and security TOR is the solution.TOR works on volunteer-operated servers. In fact you can volunteer yourself to take on this task. Using TOR, you and your target are not connected directly by recognizable Internet intermediate points but you are connected to your target by virtual tunnels. This way you can share information without compromising privacy. You can even access blocked sites.
What are use case scenarios:
- Identity thefts and unscrupulous marketing will be a thing of the past. Your identity information may leak out of your ISPs or your web surfing activities.
- Protecting your children on line who may share private information without realizing the seriousness
These above are only some of the simple scenarios that normal people use but many others have great use for such a service:
- Journalists and their audience
- Law Enforcement Officers
- High and low profile folks
- Business executives
- Bloggers
- IT Professionals
- Military
- Activists and whistleblowers
While anonymity provides a secure shield for you it can also be misused.
The safe way is to surf the internet using the Tor Browser. Don't use Torrent file-sharing applications while using Tor browser as they ignore and make direct connection. Also do not install any kind of plug-ins as they can compromise privacy. Do not open applications downloaded while using Tor Browser.
There is a possibility that Tor Browser may not work as censors may block Tor traffic even when what are called Tor bridges are used.
It is still possible to work around to use Tor Browser review this link:
https://www.torproject.org/docs/bridges.html.en
You can download the Tor Browser from the above site. Here are some screen shots of my download.
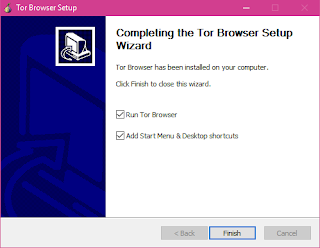
Double click the executable that you downloaded.
I used the first option by making direct connection to a Tor Network.
You can use this short cut to use your Tor Browser. I will be using mostly to do some surfing. I am not planning to visit sites that require username/password authentication.
Enjoy surfing knowing your privacy info is intact!
https://www.torproject.org/docs/bridges.html.en
You can download the Tor Browser from the above site. Here are some screen shots of my download.
Double click the executable that you downloaded.
This is where Tor files are installed.
I used the first option by making direct connection to a Tor Network.
Tor Browser starts after installation.
Enjoy surfing knowing your privacy info is intact!







No comments:
Post a Comment